We have recently enabled a new daily CoAP scan and Accessible CoAP Report. This is the third IoT related IPv4 Internet-wide scan and report implemented (after the Open MQTT scan and Open IPP scan) as part of our ongoing work in the EU CEF VARIoT project.
The new IoT scan is aimed at uncovering devices that have an exposed CoAP service running on port 5683/UDP. CoAP is a specialized web transfer protocol (similar to HTTP) for use with constrained nodes and constrained networks. As described in RFC 7252, CoAP is designed for use in machine-to-machine (M2M) applications such as smart energy and building automation.
How we scan
We scan by sending out a 21-byte CoAP CoRE Resource Discovery request: we send a CoAP GET request for /.well-known/core to the default port (5683/UDP) on all ~4 billion routable IPv4 addresses every day. The relative URI /.well-known/core acts as the default entry point for requesting the list of links about resources and returns a set of links to available services from the CoAP server (if any) using the CoRE Link Format (RFC 6690). We report only responses that have the CoAP response code set to 2.05 (“Content”).
What are the main threats associated with exposed CoAP services?
One of the main threats associated with exposed CoAP services is their possible usage as reflectors for DDoS amplification attacks (RDDoS). The average amplification factor of CoAP services has been quantified in the past at around 34. Our average measured response size to the 21-byte payload CoRE Resource Discovery request has been 569 bytes (without UDP overheads), which is roughly 27 times of the inbound request.
We also found that many of these CoAP services can leak information (including authorization credentials to services, such as wifi networks). For certain devices, in some cases, it may even be possible to issue remote instructions using CoAP.
There have also been software vulnerabilities in the past in CoAP implementations/libraries which could also potentially be abused for remote code execution on some of these exposed devices.
An in-depth study of CoAP (and MQTT) security considerations can be found in a paper published by Trend Micro.
Scan results
464,159 hosts responded to our IPv4 Internet-wide scan on the 21st of June 2020. By far, most of the responding services were from the Philippines, China and Russia. Together they accounted for nearly 93% of all the exposed instances.
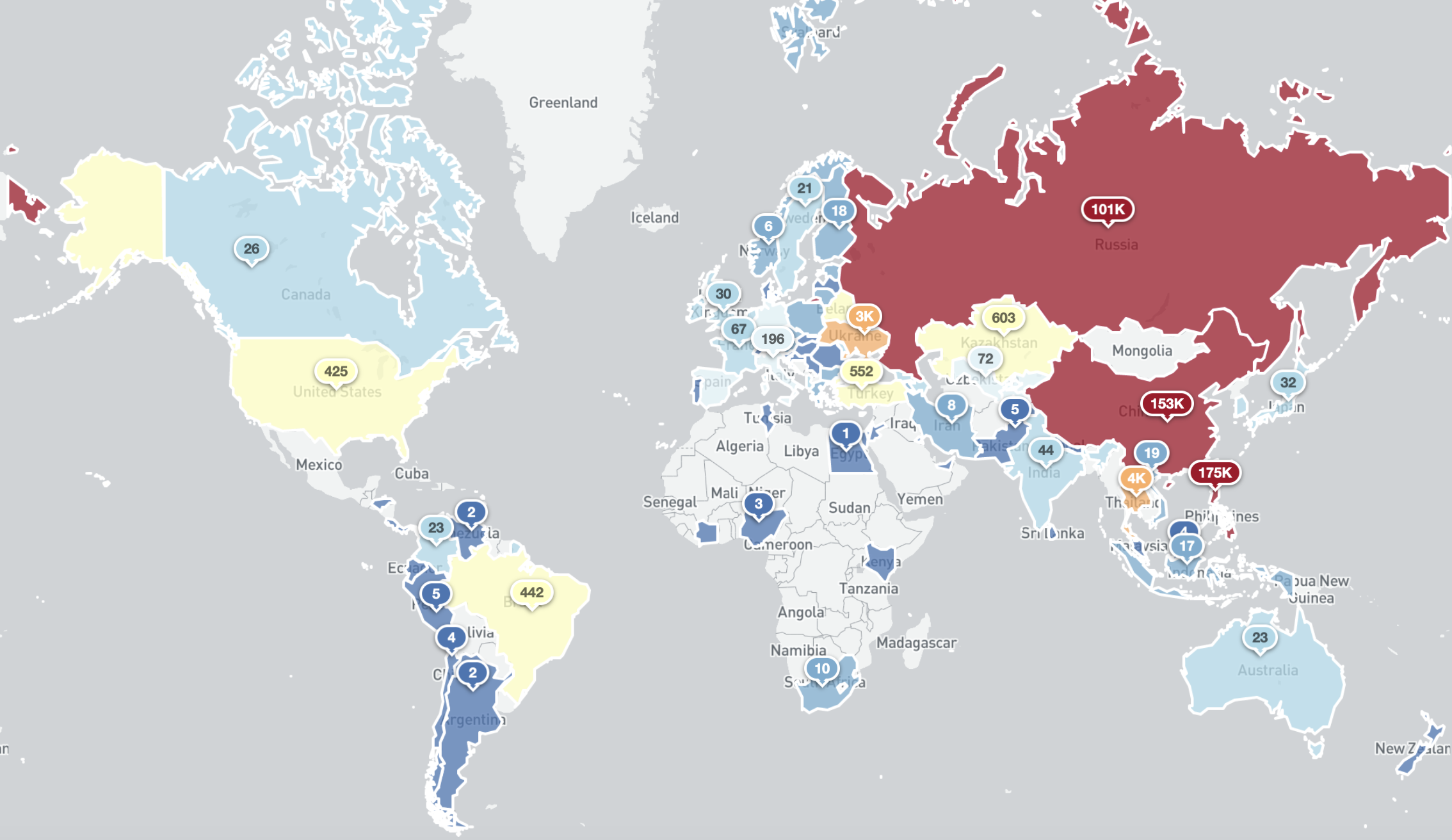
Exposed CoAP Services Around the World (21st June 2020)
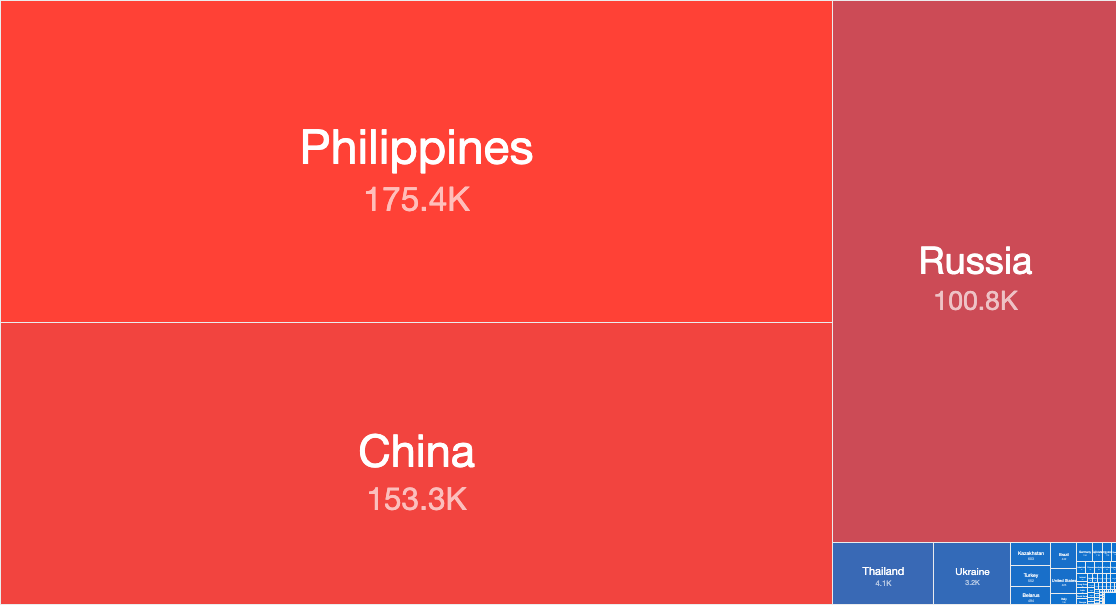
Top Countries with Exposed CoAP Services (21st June 2020)
The predominant CoAP responses returned in the Philippines and China show Qlink resources (now rebranded as QLC Chain) a “next generation public chain for Network-as-a-Service (NaaS).” In Russia (and the Ukraine), most of the CoAP responses are from devices apparently containing NDM Systems embedded software (described on its website as “a smart router software company”).
What can be done to improve the security of the exposed instances?
We hope that the data being shared in our new accessible CoAP device report will lead to a reduction in the number of exposed CoAP-aware devices on the Internet, as well as raise awareness to the dangers of exposing such devices to unauthenticated scanners/attackers. As described in RFC 7252:
“CoAP itself does not provide protocol primitives for authentication or authorization; where this is required, it can either be provided by communication security (i.e., IPsec or DTLS) or by object security (within the payload)”.
While the RFC makes a number of provisions for securing CoAP (elaborating on the above), it is unclear how many of these have actually been adopted in practice. At the very least CoAP instances should therefore be either firewalled to only communicate with necessary devices and/or DTLS (Datagram Transport Layer Security) with certificates employed where possible.
How can I receive the free new daily CoAP report?
Details about the format of the new report being shared can be found in the new Accessible CoAP Report page. All existing Shadowserver report subscribers are now automatically receiving the Accessible CoAP Report if any exposed CoAP services are identified within their networks and countries (for national CSIRTs).
If you are not already a subscriber to Shadowserver’s public benefit daily network reports and would like to receive this new Accessible CoAP report and our other existing 78 report types, then please sign up to our free daily public benefit network remediation feed service.
You can check the latest daily CoAP scan results on our dedicated CoAP scan page.

