The Kelihos botnet (and its predecessor Waledec) was one of the most active spamming botnets. Earlier versions of the malware were also involved in delivering trojan horses, stealing user credentials and crypto currency wallets, and in crypto currency mining. The Kelihos botnet was made up of a network of tens of thousands of infected Windows hosts worldwide. It used its own peer-to-peer (P2P) protocol, along with backup DNS domains, to provide resilient command and control (C2) facilities.
The Shadowserver Foundation first alerted the public to the appearance of Kelihos back in 2010 and has supported multiple botnet takedown activities over the years, which historically helped to establish industry codes of conduct for botnet takedowns.
Despite multiple prior takedown attempts in 2011, 2012 and 2013, Kelihos has continued to remain active since 2010 (or since 2008 in its previous incarnation as Waledec). The botnet has delivered large volumes (up to billions) of spam emails every day – including in recent years pump and dump scams, phishing attacks and delivery of ransomware and banking trojans. As such, Kelihos has consistently been one of the main facilitators of email based cybercrime. The alleged operator of the Kelihos botnet (and the Waledec botnet before it) was ranked #7 worst spammer globally by Spamhaus at the time of the operation and has previously been indicted in the US on multiple charges.
The Kelihos.E botnet takedown occurred on Friday April 8th 2017, with 100% of the peer-to-peer network being successfully taken over by law enforcement and C2 traffic redirected to our sinkholes, C2 backend server infrastructure being seized/disrupted, as well as multiple fallback DNS domains being successfully sinkholed under US court order. An arrest was made by Spanish police in Barcelona, Spain.
The Shadowserver Foundation once again participated in the takedown of the Kelihos botnet (in this case variant “Kelihos.E”) by providing the US Federal Bureau of Investigation (FBI) and security researchers at CrowdStrike with infrastructure and support, and gathering data on infected clients for the purposes of victim notification and remediation.
During the first five days of the Kelihos.E takedown operation we observed:
- 222,792 unique IP address connecting to the sinkholes
- 119,636 unique IP addresses making P2P bootstrap requests to the sinkholes, from 45,983 unique BotIDs
- 34,542 unique IP addresses involved in “harvest” botnet commands
- 141,213 unique IP addresses involved in “job” botnet commands
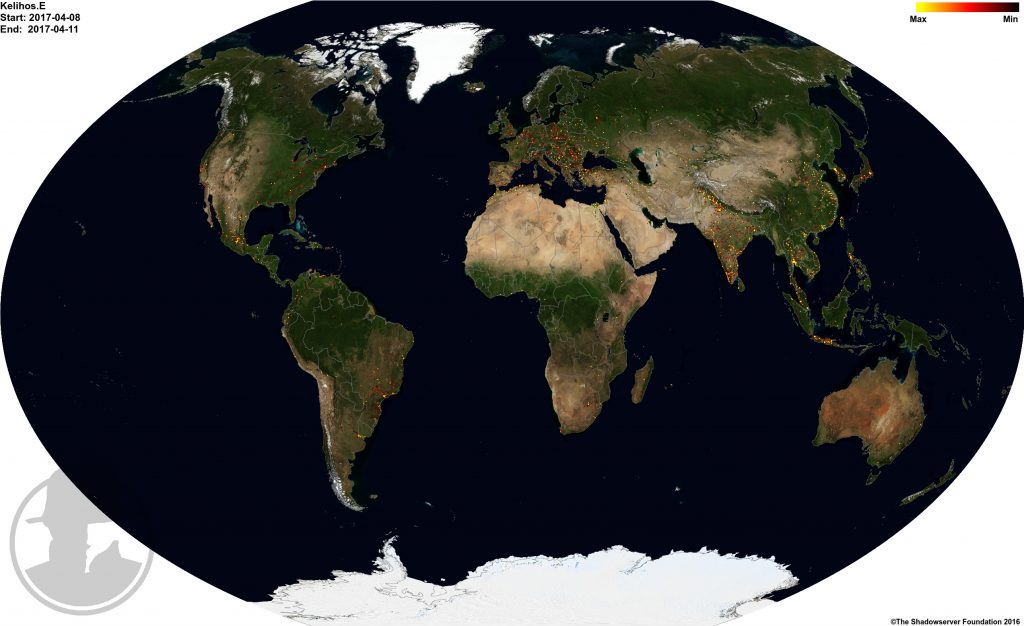
The initial global distribution of unique IP addresses infected with Kelihos.E was:
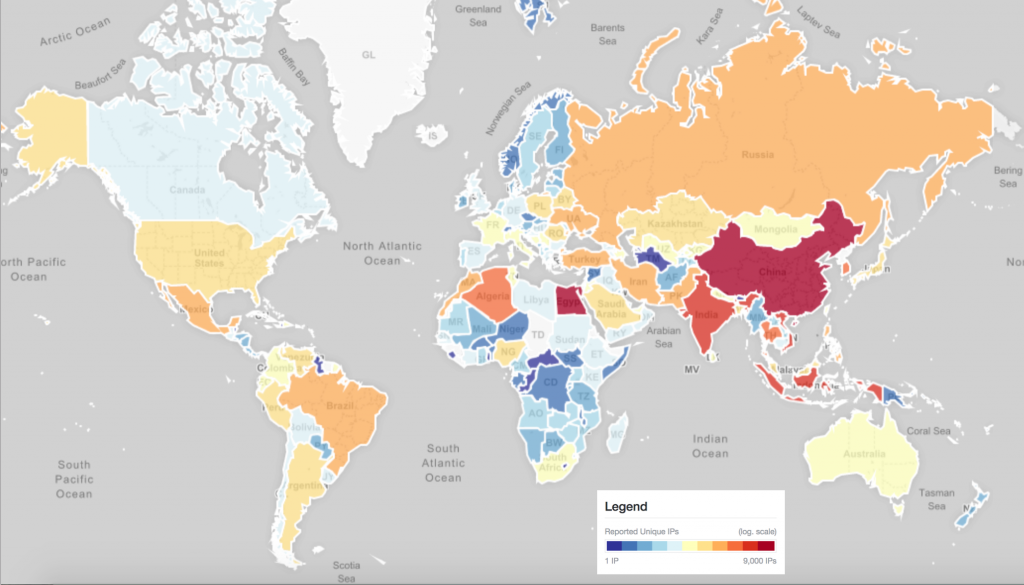
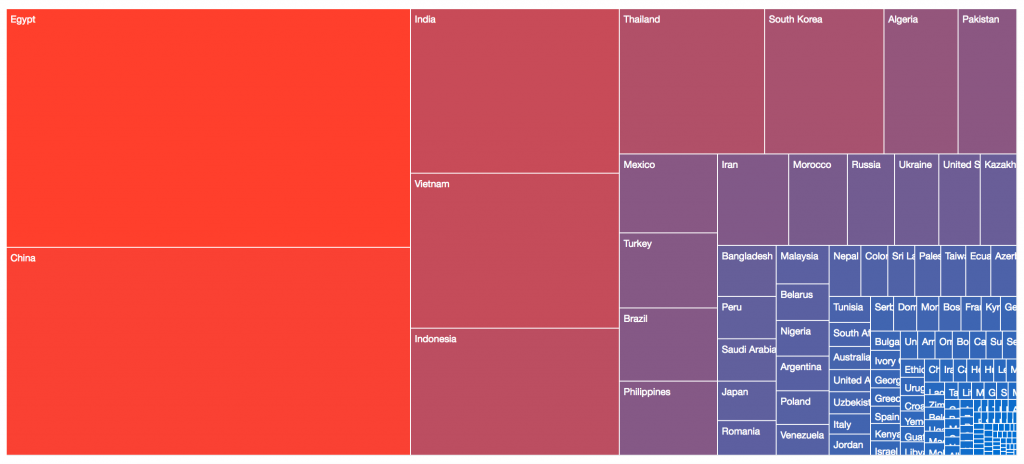
The initial geographic distribution showed a number of international hot spots:
You can find further statistics on our regularly updated Kelihos.E public statistics site.
The Shadowserver Foundation will continue to work with National CERTs and network owners to remediate the infected computers. For existing Shadowserver report consumers, the Kelihos.E infections will be tagged as “kelihos.e” in the Drone report.
If you do not already receive our free of charge remediation data for your network(s), you can obtain our free nightly reports about compromised and misconfigured devices identified on your networks by signing up for them here.