Introduction
On 15 September 2015, FireEye published information about potentially compromised Cisco routers under the name SYNful Knock. As soon as Shadowserver became aware of these potential compromises, Shadowserver and Cisco worked together and cooperated to scan the internet to detect these affected routers to allow a more accurate notification of the affected end-users. We are pleased to partner with Cisco on its response to SYNful Knock. Cisco supported the initial public disclosure of this malware and has created an Event Response Page for its customers.
Statistics
To date, Shadowserver has identified 199 unique IP addresses that match the SYNful Knock behavior. This table shows the results of the scan from 2015-09-20 which had 163 unique systems:
Table of Geographical Distribution
| Country | CC | Total |
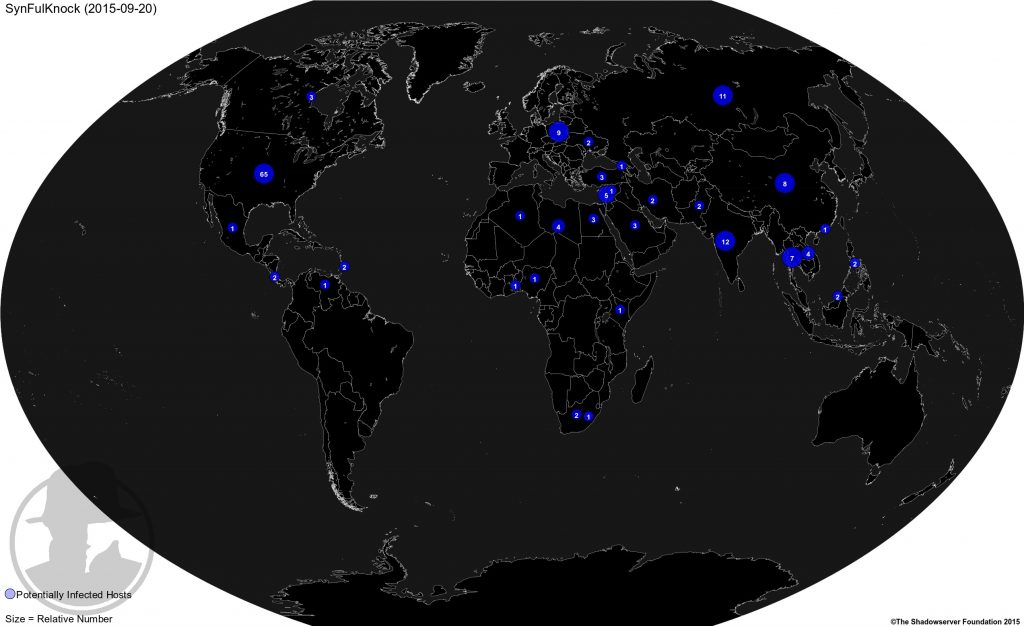
| United States | US | 65 |
| India | IN | 12 |
| Russian Federation | RU | 11 |
| Poland | PL | 9 |
| China | CN | 8 |
| Thailand | TH | 7 |
| Lebanon | LB | 5 |
| Libya | LY | 4 |
| Vietnam | VN | 4 |
| Turkey | TR | 3 |
| Saudi Arabia | SA | 3 |
| Egypt | EG | 3 |
| Canada | CA | 3 |
| Iran, Islamic Republic of | IR | 2 |
| Philippines | PH | 2 |
| Pakistan | PK | 2 |
| Ukraine | UA | 2 |
| Brunei Darussalam | BN | 2 |
| Barbados | BB | 2 |
| Costa Rica | CR | 2 |
| South Africa | ZA | 2 |
| Syrian Arab Republic | SY | 1 |
| Togo | TG | 1 |
| Nigeria | NG | 1 |
| Kenya | KE | 1 |
| Algeria | DZ | 1 |
| Mexico | MX | 1 |
| Venezuela | VE | 1 |
| Hong Kong | HK | 1 |
| Georgia | GE | 1 |
| Lesotho | LS | 1 |
| Total | 163 |
Map of Geographical Distribution
We will continue scanning and updating the statistics. Shadowserver will begin notifying consumers through our normal reporting mechanisms starting 21 September 2015. Existing consumers will receive daily reports. New consumers can sign up for reports by following the instructions here.
Impact
It is important to stress the severity of this malicious activity. Currently, Shadowserver believes that any machine that responds to this scan is potentially compromised. Compromised routers should be identified and remediated as a top priority.
Remediation
Prevention
- Step 1: Harden devices – use Cisco’s guidance to harden Cisco IOS devices
- Step 2: Instrument the network – follow recommendations Telemetry-Based Infrastructure Device Integrity Monitoring
- Step 3: Establish a baseline – ensure operational procedures include methods to establish a baseline
- Step 4: Analyze deviations from the baseline by leveraging technical capabilities and recommendations for Cisco IOS Software Integrity Assurance.
Monitoring
Shadowserver also encourages network administrators to monitor for this activity on their network. Snort rules are available from here. This will allow monitors to identify compromised machines within their network.
According to FireEye, “The initial infection vector does not appear to leverage a zero-day vulnerability. It is believed that the credentials are either default or discovered by the attacker in order to install the backdoor. However, the router’s position in the network makes it an ideal target for re-entry or further infection.”