Open IPP Report - Exposed Printer Devices on the Internet
June 10, 2020
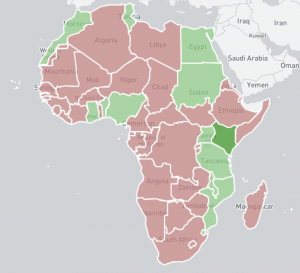
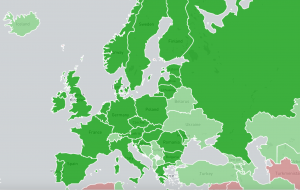
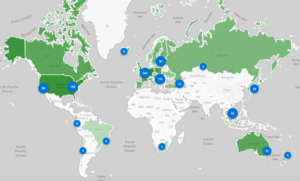
We have enabled a new scan dedicated to finding open IPP (Internet Printing Protocol) devices exposed on port 631/TCP. The roughly 80,000 devices uncovered as a result of the scan have connected to the Internet without adequate access controls or authorization mechanisms in place. This could allow for a potential range of different types of attacks, from information disclosure and service disruption/tampering, to, in some cases, remote command execution. Results of the scan are collected in the new Open IPP report. This is the second scan enabled under the EU CEF VARIoT project.